Today, people’s identities online are just as important (if not more) as it is offline. In most regions, internet has penetrated the very fabric of society where people use it for a several purposes including social networking, financial planning, healthcare, logistics, education, and more.
But the information age has made it exceedingly easy for folks with malicious intent to take advantage of the still-developing identity verification infrastructure or big data companies selling sensitive KYC data to profit-driven conglomerates.
Whenever we visit a website or application, we are obliged to consent to the use of our data. In most cases, you have no choice. If you fail or decide not to click that button, you will be expelled from using the application or accessing the website.
The mass engagement of the internet results in our continuous uploading of our data. This makes it difficult for users to track and manage them all. Meanwhile, controlling where and when you use your data online is important in a digital world.
The good thing is that this is changing. And decentralization is gradually replacing centralization where the concern of central data storage is becoming a thing of the past.
So, in this instance, how can users regain control of their digital identities? The solution relies on the introduction of more decentralized systems of identity management.
What is the Decentralized Identity Model and How Does It Work?
Decentralized identity brings digital freedom to users. It brings advancements for users to regain control over their data on the internet.
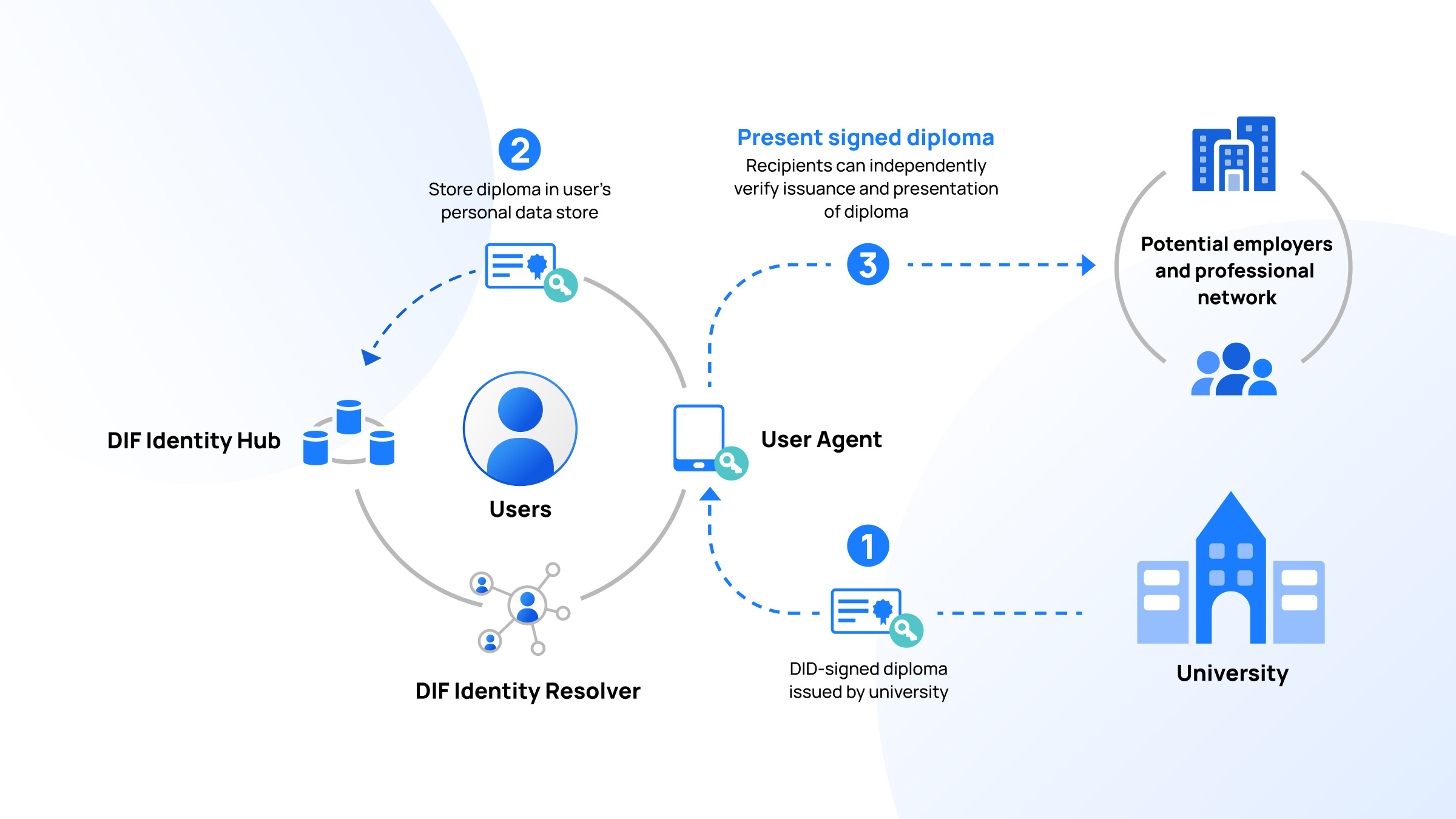
Unlike traditional identity systems that rely on centralized entities, authorities, and databases to own and manage identity data, decentralized identities leverage the transparency and security of blockchain.
With decentralized identities, your personal data is end-to-end encrypted and securely stored on a distributed, tamper-proof system. This approach gives you full control over your personal information.
Decentralized identities allow you to own and manage your personally identifiable information, enabling you to disclose only the information necessary for a particular transaction.
This enhances privacy and reduces the need to share sensitive data with identity providers. By embracing decentralized identity management, you gain freedom from traditional constraints and benefit from a more secure digital presence.
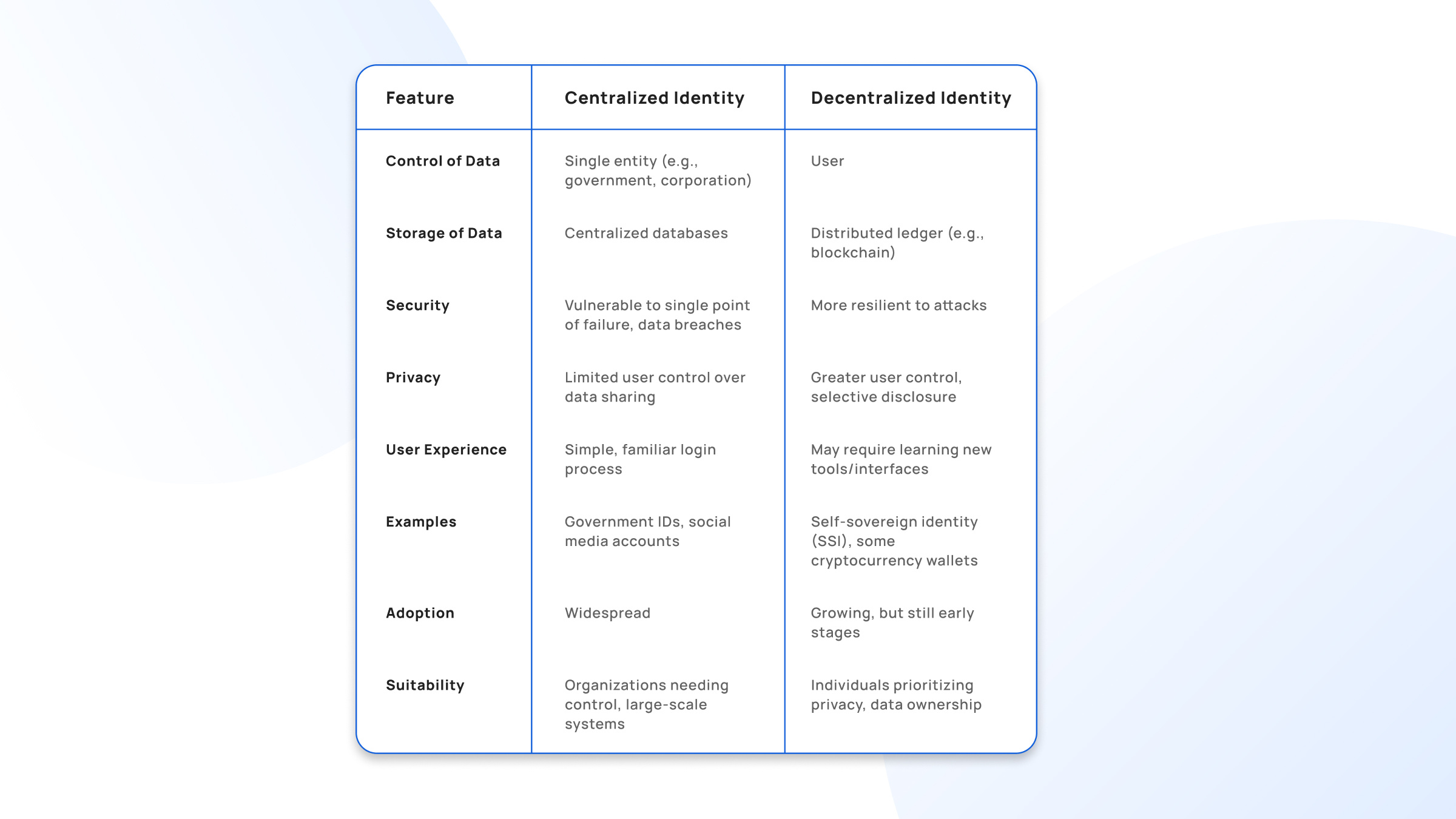
Centralized vs. Decentralized: Key Differences
Both centralized identity providers and decentralized, secure identity verification and management systems denote two fundamentally distinct paradigms.
Core Componenets of Decentralized Identities
There are three core components of decentralized identities:
- Decentralized identifiers
- DID documents
- Verificable Credentials (VCs)
1. Decentralized Identifiers
DIDs are Uniform Resource Identifiers (URIs) that conform to a specific syntax defined in the DID Core specification. They typically consist of three parts:
- did: The URI scheme identifier.
- method: A string identifying the specific DID method used to create and resolve the DID.
- method-specific identifier: A unique string that identifies the DID subject within the context of the DID method.
DID methods are modular components that define how DIDs are created, resolved, and managed. They determine the underlying technology and protocols used for DID operations. Examples include:
- did:sov: Utilizes Hyperledger Indy and Sovrin for blockchain-based DID management.
- did:ion: Based on the Sidetree protocol and leverages the Bitcoin blockchain for anchoring.
- did:web: Allows for DIDs to be associated with web domains.
DID resolution is the process of retrieving a DID document associated with a DID. It typically involves querying a DID resolver, which may interact with different systems (e.g., blockchains, distributed ledgers) depending on the DID method.
2. DID Documents
DID documents are typically represented in a standard format like JSON-LD. They contain structured data that describes the DID subject and its associated resources.
Key Components of DID documents:
- @context: Defines the JSON-LD context, including vocabulary and terms used in the document.
- id: The DID itself.
- controller: (Optional) Indicates the DID that controls the document.
- verificationMethod: An array of verification methods (public keys) associated with the DID subject.
- authentication: An array of verification methods that can be used for authentication purposes.
- assertionMethod: An array of verification methods that can be used for making assertions about the DID subject.
- keyAgreement: An array of verification methods that can be used for establishing secure communication channels.
- service: An array of service endpoints that can be used to interact with the DID subject.
Verification methods define how cryptographic operations can be performed with the DID document. They can include different types of keys (e.g., Ed25519, RSA) and signature algorithms (e.g., EdDSA, RSASSA-PKCS1-v1_5).
3. Verifiable Credentials (VCs)
VCs are typically encoded in JSON-LD and follow the Verifiable Credentials Data Model. They contain the following key elements:
- @context: Defines the context and terms used in the VC.
- id: A unique identifier for the VC.
- type: An array of strings indicating the type of VC (e.g., "VerifiableCredential", "UniversityDegreeCredential").
- issuer: The DID of the entity that issued the VC.
- issuanceDate: The date and time the VC was issued.
- credentialSubject: The DID subject of the VC, along with the claims being made about them.
- proof: A cryptographic proof that binds the VC to the issuer and ensures its integrity.
VCs are typically signed using digital signatures. The type of signature depends on the verification method used by the issuer, like Transak for Polygon ID.
VCs enable selective disclosure, allowing users to share only the necessary information with verifiers — that is how you can be sure that when you sign in using Polygon ID and verify with Transak, your personal data is not overshared or exploited.
Benefits of Decentralized Identities for Individuals
1. Enhanced Privacy and Control
Decentralized identities use cryptographic principles and blockchain technology to ensure that individuals have full control over their personal data.
Individuals can choose what information to share and with whom, reducing the risk of data exposure and enhancing privacy. This user-centric approach prevents unauthorized access and misuse of personal information.
2. Data Ownership and Portability
Decentralized identity systems utilize decentralized identifiers (DIDs) and verifiable credentials (VCs) that are controlled by the individual. These credentials can be used across different services without needing to recreate accounts or re-enter information.
Individuals retain ownership of their identity data and can move seamlessly between different platforms and services, improving user experience and reducing redundancy.
3. Reduced Risk of Identity Theft
Blockchain's immutability and decentralized nature make it exceedingly difficult for malicious actors to alter or counterfeit identity information. Each transaction or modification of data is recorded transparently and cannot be changed retroactively.
The robust security framework of blockchain minimizes the chances of identity theft, providing individuals with greater peace of mind regarding their personal information's safety.
4. Trust and Security
The decentralized nature of blockchain ensures that there is no single point of failure, and the consensus mechanisms validate transactions across the network. This decentralized trust model is more secure than traditional centralized systems where a breach of a single point can compromise the entire system.
Users can trust that their identity information is secure and has not been tampered with, fostering confidence in online interactions and transactions.
Benefits of Decentralized Identities for Organizations
1. Improved Security
Decentralized identities eliminate the need for centralized databases, which are often targets for hackers. Data is encrypted and stored across a distributed ledger, making unauthorized access and data breaches significantly harder.
Organizations can assure their users that their personal information is safe, enhancing the trustworthiness of their apps and services.
2. Simplified Compliance
Regulations such as GDPR require strict handling of personal data, including user consent and the right to be forgotten. Decentralized identity systems inherently provide these features, as users control their own data and can manage consent independently.
Compliance with data protection regulations becomes more straightforward, reducing legal risks and potential fines for the organization.
3. Cost Efficiency
Maintaining and securing centralized identity databases requires significant resources and ongoing costs for security updates, infrastructure, and personnel. Decentralized systems distribute these responsibilities across the network, reducing the burden on individual organizations.
Lower operational costs associated with identity management, allowing organizations to allocate resources more efficiently.
4. Interoperability
Decentralized identities are designed to be interoperable across different platforms and services through standardized protocols like DIDs and VCs. This allows for seamless integration and user authentication across various systems.
Organizations can develop applications that easily integrate with other services, enhancing the user experience and broadening their ecosystem.
Closing Thought
Internet evolution continues. And digital identity plays a key role in almost all that we do on the internet every day. It governs so much of the services provided to us on the Internet. Have you ever wondered how important digital identity is in our daily lives? If the answer is yes, then some clear examples of how it is that we use it to purchase travel tickets, order meals, and even check into hotels. It’s quite impossible to access these services without providing identity oneself.

